Threat Modeling for SaMD: A Step-by-Step Guide to Compliance with MDR and FDA Regulations
In the rapidly evolving field of Software as a Medical Device (SaMD), ensuring cybersecurity is paramount. For example in 2023 more than 40 million US citizens were affected by data breaches in healthcare. Regulatory bodies like the FDA and Competent Authorities governing the Medical Device Regulation (MDR) in the EU (refer to MDCG2019-16 rev 1) mandate adherence to threat modeling – a pivotal element in the cybersecurity risk management framework.
Within this blogpost we offer a practical walkthrough for organizations looking to develop a threat modeling strategy that aligns with these requirements.
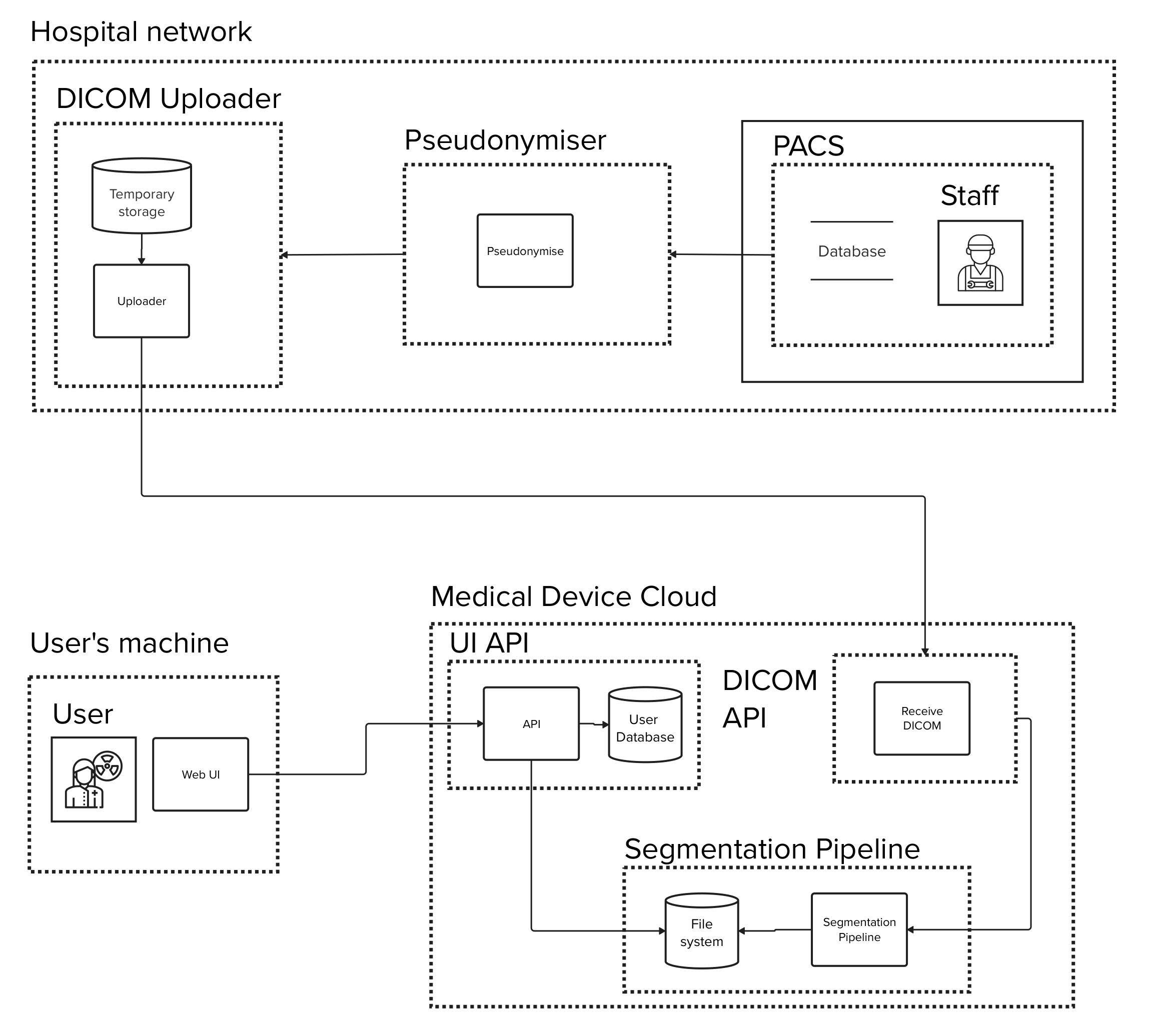
At the heart of our exploration is a fictional device:
'a cloud-based platform designed to segment and analyze DICOM data received from a hospital's PACS system and visualize the results through an interactive web application'
This system, depicted on the right, represents the intricate network of data exchange between hospital networks, cloud services, and end-users.
It provides a snapshot of our device's architecture, serving as the groundwork for the detailed Data Flow Diagram and subsequent threat modeling activities.
Incorporating threat modeling from the initial phases of SaMD development is crucial. It necessitates a deliberate approach to planning, compelling developers to integrate cybersecurity considerations into their software development plans. Creating a dedicated cybersecurity plan, or embedding these considerations within the broader development plan, is not merely advantageous—it's essential. Such proactive planning is the key to preempting costly post-development modifications, ensuring that security is an integral, foundational element of the device's architecture. This foresight facilitates a smoother progression toward developing a secure, compliant SaMD.
As we proceed, this guide will unravel the complexities of threat modeling, ensuring that organizations are equipped to navigate the challenges of securing SaMDs in alignment with MDR and FDA regulations.